This is Why People [SHOULD] Fear the ‘Internet of Things’
 Thursday, February 18, 2016 at 12:25PM
Thursday, February 18, 2016 at 12:25PM This is Why People Fear the ‘Internet of Things’

The FI9286P, a Foscam camera that includes P2P communication by default.
This is the nightmare “Internet of Things” (IoT) scenario for any system administrator: The IP cameras that you bought to secure your physical space suddenly turn into a vast cloud network designed to share your pictures and videos far and wide. The best part? It’s all plug-and-play, no configuration necessary!
I first became aware of this bizarre experiment in how not to do IoT last week when a reader sent a link to a lengthy discussion thread on the support forum for Foscam, a Chinese firm that makes and sells security cameras. The thread was started by a Foscam user who noticed his IP camera was noisily and incessantly calling out to more than a dozen online hosts in almost as many countries.
Turns out, this Focscam camera was one of several newer models the company makes that comes with peer-to-peer networking capabilities baked in. This fact is not exactly spelled out for the user (although some of the models listed do say “P2P” in the product name, others do not).
But the bigger issue with these P2P -based cameras is that while the user interface for the camera has a setting to disable P2P traffic (it is enabled by default), Foscam admits that disabling the P2P option doesn’t actually do anything to stop the device from seeking out other P2P hosts online (see screenshot below).
This is a concern because the P2P function built into Foscam P2P cameras is designed to punch through firewalls and can’t be switched off without applying a firmware update plus an additional patch that the company only released after repeated pleas from users on its support forum.
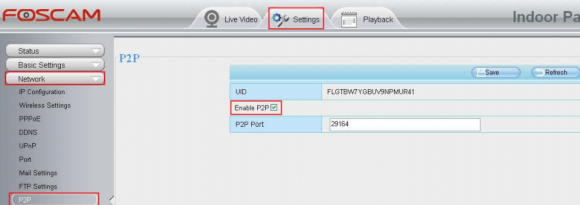
Yeah, this setting doesn’t work. P2P is still enabled even after you uncheck the box.
One of the many hosts that Foscam users reported seeing in their firewall logs was iotcplatform.com, a domain registered to Chinese communications firm ThroughTek Co., Ltd. Turns out, this domain has shown up in firewall logs for a number of other curious tinkerers who cared to take a closer look at what their network attached storage and home automation toys were doing on their network.
In January 2015, a contributing writer for the threat-tracking SANS Internet Storm Centerwrote in IoT: The Rise of the Machines that he found the same iotcplatform.com domain called out in network traffic generated by a Maginon SmartPlug he’d purchased (smart plugs are power receptacles into which you plug lights and other appliances you may wish to control remotely).
What is the IOTC Plaform? According to ThroughTek, it’s a service developed to establish P2P communications between devices.
“I read the documentation provided with the device as well as all the website pages and there is no mention of this service,” wrote Xavier Mertens, an incident handler and blogger for SANS. “Manufacturers should include some technical documentation about the network requirements (ex: to download firmware updates).”
In another instance from May 2015, this blogger noted similar communications trafficemanating from a digital video recorder (DVR) device that’s sold in tandem with Internet-enabled surveillance cameras made by a company called Swann.
Likewise, postings from Dec. 2014 on the QNAP network attached storage (NAS) user forum indicate that some QNAP customers discovered mysterious traffic to iotcplatform.com and other Internet address requests that also were found in the Swann and Smart Plug traffic.
What do all of these things have in common? A visit to ThroughTek’s Web lists several “case studies” for its products, including Swann, QNAP and a home automation company based in Taiwan called AboCom.
A ThroughTek press release from October 2015 announced that the company’s P2P network — which it calls the Kalay Network — had grown to support more than seven million connected devices
ThroughTek did not respond to requests for comment. A ThroughTek press release from October 2015 announced that the company’s P2P network — which it calls the Kalay Network — had grown to support more than seven million connected devices and 100 million “IoT connections.”
I contacted Foscam to better understand the company’s relationship to ThroughTek, and to learn just how many Foscam devices now ship with ThroughTek’s built-in, always-on P2P technology. Foscam declined to say how many different models bundled the P2P technology, but it’s at least a dozen by my count of the models mentioned in the Foscam user manual and discussion thread.
Foscam customer service representative David Qu wrote in reply to requests for comment that “ThroughTek provides P2P technical support service for us.” He also said the P2P cameras merely keep a “heartbeat” connection to Foscam’s P2P server to check the connection status with the servers, and that no camera data will be stored on the company’s servers.
“The details about how P2P feature works which will be helpful for you understand why the camera need communicate with P2P servers,” Qu explained. “Our company deploy many servers in some regions of global world.” Qu further explained:
1. When the camera is powered on and connected to the internet, the camera will log in our main P2P server with fastest response and get the IP address of other server with low load and log in it. Then the camera will not connect the main P2P server.
2. When log in the camera via P2P with Foscam App, the app will also log in our main P2P server with fastest response and get the IP address of the server the camera connect to.
3. The App will ask the server create an independent tunnel between the app and the camera. The data and video will transfers directly between them and will not pass through the server. If the server fail to create the tunnel, the data and video will be forwarded by the server and all of them are encrypted.
4. Finally the camera will keep hearbeat connection with our P2P server in order to check the connection status with the servers so that the app can visit the camera directly via the server. Only when the camera power off/on or change another network, it will replicate the steps above.”
As I noted in a recent column IoT Reality: Smart Devices, Dumb Defaults, the problem with so many IoT devices is not necessarily that they’re ill-conceived, it’s that their default settings often ignore security and/or privacy concerns. I’m baffled as to why such a well-known brand as Foscam would enable P2P communications on a product that is primarily used to monitor and secure homes and offices.
Apparently I’m not alone in my bafflement. Nicholas Weaver, a senior researcher in networking and security for the International Computer Science Institute (ICSI), called the embedded P2P feature “an insanely bad idea” all around.
“It opens up all Foscam users not only to attacks on their cameras themselves (which may be very sensitive), but an exploit of the camera also enables further intrusions into the home network,” Weaver said.
“It opens up all Foscam users not only to attacks on their cameras themselves (which may be very sensitive), but an exploit of the camera also enables further intrusions into the home network,” Weaver said.
“Given the seemingly cavalier attitude and the almost certain lack of automatic updates, it is almost certain that these devices are remotely exploitable,” he added. “It is no wonder that Director of National Intelligence James Clapper is worried about the Internet of Things, how many government officials have or may unwittingly install potential spies like this in their home.”
If you’re curious about an IoT device you purchased and what it might do after you connect it to a network, the information is there if you know how and where to look. This Lifehacker post walks through some of the basic software tools and steps that even a novice can follow to learn more about what’s going on across a local network.
By Brian Krebs





